AILUX: TECHNOLOGY MANUFACTURER
For 20 years, we have been developing communication systems and automations for balancing, stability and security of electricity and gas grids, guaranteeing the well-being of companies and the community with innovative, customised solutions that comply with the technical specifications of Terna, Enel and Snam.

TEAM OF
ENGINEERS
SOLUTIONS
CUSTOMISED
ASSISTANCE
H24

CERTIFIED COMPANY
Our company
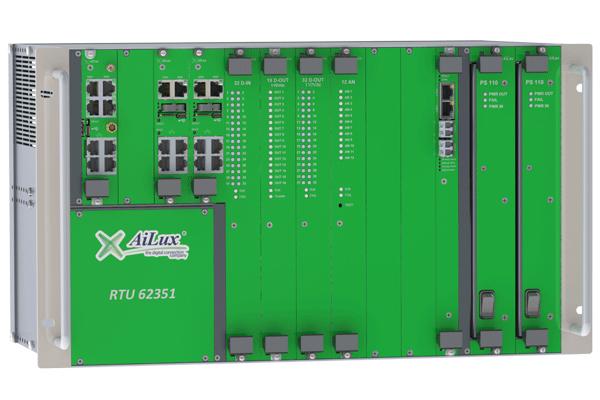
We are a technology manufacturer and our mission is to make RTU Remote Terminal Units for electrical substations, primary and secondary substations.
We are part of the international technical committee IECTC57WG15 for the drafting of the IEC62351 secure communication protocol standard, used in the electrical and energy fields.
- DNV-GL Certifications
- Laboratory Certifications
- Quality Certifications

TECHNICAL ASSISTANCE
We always pay close attention to customer needs and satisfaction. That is why our engineers, specialised in the implementation of communication protocols, are at your disposal to solve any kind of requirement with innovative solutions in the shortest possible time.
- Help Desk: Telephone and telematic support service
- H24 support: Service for companies that operate on a continuous cycle and also need immediate intervention with predefined SLAs

BECAME PARTNER
The AiLux partnership programme offers you the opportunity to promote our solutions and products, infrastructures, customised equipment, systems and services developed by our engineering staff for the electrical and energy sector.
Ask for an appointment with our technical sales staff to discuss this opportunity: we will be happy to explain our partnership proposal in detail.
The markets we address
OIL & GAS
We develop integrated control and automation systems for oil & gas plants
ENERGY AUTOMATION
We develop control systems for electrical substations, primary and secondary substations
SMART GRID
We develop smart grids for the intelligent, secure and rational distribution of electricity
SYSTEM INTEGRATOR

We connect plants that optimise production plants
MULTIUTILITY
We cooperate with utilities in the convergence process
INTERNET OF THINGS

We work with smart devices that optimise monitoring and data collection
RENEWABLES
We look to the future by installing UPDM in Italy’s leading photovoltaic and wind farms
ENERGY COMMUNITIES
Encouraging collaborative forms of energy to foster sustainable development
Our solutions
A variety of customised solutions developed with the most innovative technologies and implemented for the relevant sector.
TELECONTROL
TELESCATTO

Remote control and telescope system
ANNEXES
TERNA CDR

Development of RTU compliance CDR Terna solutions
FAST RESERVE
SART TENSION ADJUSTMENT

Frequency / voltage control verification system
MSD FLEXIBILITY
ENERGETICS
Terna Dispatching Services Market
INTERRUPTIBILITY
ENERGY PRODUCERS

Electricity and gas supply interruptibility system
ENERGY
MONITORING

Energy consumption monitoring system
AS A SERVICE

Solutions on loan for use
COLOCATION
& HOSTING

The data center for the electricity and energy market
Some of our customers






Associated company